What You Need to Know About Backoff - Jeffrey Roman - Data Breach
This post first appeared on Exploring Information Security.
What You Need to Know About Backoff - Jeffrey Roman - Data Breach
This post first appeared on Exploring Information Security.
In the seventh edition of the Exploring Information Security (EIS) podcast, I talk with Zed Attack Proxy (ZAP) creator and project lead Simon Bennetts.
Simon is the project lead for ZAP an OWASP Open Web Application Security Project. He has a developer background and originally built the tool to help developers build better applications. The tool was so good that it caught the eye of the security community and is now used by developers, people just getting into security and veteran pen testers. You can follow him on Twitter @psiinon and find out more on the tool by going to the project site on OWASP.
In this interview we cover:
What is ZAP and how did the project get started?
Who should utilize ZAP?
What skill level is need to start using ZAP?
Where should ZAP be used?
How you can get involved in the project.
Music by Alan Read
Leave feedback and topic suggestions in the comment section below.
This post first appeared on Exploring Information Security.
The last week I've been stressing out over a Spanish project that was due this evening. As such, I was unable to get something up for this morning. I have since submitted my project for grading and I am now free to post some content on this website.
A couple things.
Home Depot confirms breach but stays mum as to size - Robert Lemos - ars technica
Monday Home Depot confirmed what we all suspected, they had their point-of-sale (PoS) terminals compromised. If you have shopped at a Home Depot in either the U.S. or Canada at some point in the last five months, all the way back to April, then your credit card was likely stolen by online criminals. Call your bank and have a new card issued.
Unfortunately, this is one of those situations where you did nothing wrong (other than shop at Home Depot, BAZINGA!) and you got your financial information compromised. However, there are some thing you can do to help protect your financial well-being, which I wrote about yesterday.
We're in the battle for the net - battleforthenet.com
The internet service providers (ISPs) such as Comcast, Verizon, Time Warner Cable and AT&T are trying to have the FCC restructure regulations so that they can provide two lanes with differing speeds for sites on the internet.
Net neutrality (also network neutrality or Internet neutrality) is the principle that Internet service providers and governments should treat all data on the Internet equally, not discriminating or charging differentially by user, content, site, platform, application, type of attached equipment, and modes of communication.
If ISPs are allowed to regulate the internet, then we essentially lose our freedom on the internet. If you want to get a better understanding of the situation, here is John Oliver's take on the whole issue. It's 15 minutes long, but worth it.
This post first appeared on Exploring Information Security.
As much as I would like to give out a sigh of relief that I don’t shop at Home Depot, I just can’t. While it’s likely that Home Depot has been breached, it’s only one store of many. I shop at its competitor Lowe’s and Sam’s and restaurants and various other services. In the last 10 months we’ve seen several vendors release statements that they have been breached. From Target to Dairy Queen to Goodwill to UPS to Home Depot and several other stores in between. The latest threat to my financial security is the places I shop.
Last month the U.S. government has warned that over 1,000 companies have had their point-of-sale systems compromised with malware intent on stealing credit and debit card information. I shopped at Target during the three weeks they got breached and had to have my card replaced. I’ve managed to dodge the bullet since then, but I expect that at some within the next year I’ll be calling my bank again for a new credit card.
Since it’s not feasible to stop shopping at local stores, here are some of the things that I try to do to protect myself from breaches that could put my financial well-being at risk.
Use a credit card instead of a debit card
Anywhere I shop, be it online or offline, I always try to use a credit card. If my credit card gets stolen in one of these breaches, criminals will have access to by credit line, not my personal bank account. I feel much more confident that I can get the charges on my credit card dropped with less stress and much less hassle than trying to recover money from my drained bank account.
Check your statements
Whether it is credit card or a debit card, I try to keep an eye on my bank statements. At least once a week I will login to my bank account and go through my credit card and checking account statements. Any rogue transactions get reported with the simple click of a button (your bank process may vary). I’ve benefited from this by also finding a couple transactions that a vendor had billed me twice for.
When I go through my bank statements, I am double checking every transaction, not just foreign transactions. Banks have alerts and alarms setup for transactions outside of a customer’s geographical area. Criminals have adjusted to this tactic and now sell and buy cards within a person’s geographical, which make it much tougher for banks to identify credit cards that may have been stolen.
Until companies that we buy from improve the security of their systems my financial well-being and your financial well-being will be at high risk of being compromised. We must remain vigilant in doing what we can to protect it.
This post first appeared on Exploring Information Security.
What Are Hackers Thinking? - Abigail Wang - PC Magazine
This post first appeared on Exploring Information Security.
As is the case with any big news, criminals and nefarious types are taking advantage of the celebrity nude photos news to get malware installed on the machines of the unwitting.
Celeb nude photos now being used as bait by Internet criminals - Sean Gallagher - ars technica
Links are being spread among social media sites such as Twitter and Facebook. I imagine they're also being spread on other social media platforms. Just don't do it, unless you're prepared to lose more than just your dignity.
This post first appeared on Exploring Information Security.
Aaron's Law Is Doomed Leaving US Hacking Law 'Broken' - Thomas Brewster - Forbes
There are various reasons for the impasse. One is that the plans simply haven’t elicited much interest from lawmakers or the general public, said Orin Kerr, professor of law at the George Washington University Law School. “This reform only captured the attention of a small group of people. It’s not an issue that resonates with the public – at least yet,” Kerr told me.
Privacy Under Fire: Aaron Sorkin Saw It Coming In 1999 - Bill Brenner - Liquidmatrix
In the episode, Bartlet has nominated a man for the Supreme Court whose writings suggest a lack of regard for Americans’ right to privacy. During a heated Oval Office discussion, presidential advisor Sam Seaborn explains why their candidate’s views will be dangerous in the first part of the 21st century.
These 3-D Printer Skeleton Keys Can Pick High-Security Locks in Seconds - Andy Greenberg
Even so, bump keys have long been tough to create for high security locks that use obscure, complex key blanks. Many lock makers carefully trademark or patent their key blank designs and prevent them from being sold to anyone outside a small group of verified customers. But with the advent of 3D printing, those restrictions can’t stop lockpickers from 3D printing their own blanks and filing them into bump keys—or simply printing bump keys with their teeth already aligned with a lock’s pins. In this video, Holler demonstrates a 3D-printed and filed bump key for an Ikon SK6, a key that uses restricted, carefully contorted blanks that can’t even be created by many key-milling machines.
This post first appeared on Exploring Information Security.
I am a media arts student who works in information security.
Coming out of high school I knew I was going into the military. I didn't know a lot about myself back then, but I knew that if I went to college it would be a waste of my parents money. Once I completed my service in the Navy, I decided that I was going to go straight into the workforce. I mean who wouldn't want a fresh military veteran with six years of experience working on electronics instead of some wet behind the ears kid fresh out of college. So I naively entered the workforce and things didn't go exactly as I planned as far as landing a job, but I eventually worked my way up the IT ladder to the security position I currently hold.
During that climb I did make the decision to apply for college on a part-time basis. I had paid into the GI Bill so there was no reason not to. One class a semester was easy enough, but likely meant I wouldn't be finishing college in under 20 years. That changed when the government decided to change the way the GI Bill worked. Instead of just getting my classes paid for, I was going to get my classes paid for and extra money each month I was in school. The only catch was that I needed to take over six hours a semester which was roughly three classes. Not exactly easy, but also not impossible.
Initially, when I started taking classes I had decided that I wasn't going to go for a tech degree. I had worked with electronics and IT systems for six years while in the Navy. If I was going to take classes, I wanted to learn something new. I ended up in the media arts degree program.
I don't regret the choice.
I would love to have a tech degree for career advancement purposes, but most job postings include the 'or education can be substituted with experience' caveat and I have plenty of that. A media arts degree isn't ideal for a technical career and I wouldn't recommend it to anyone, however, I do think it has it's benefits. Attention to detail is something the military taught me and my media arts degree has helped me refine. Every excellent piece of work you see or hear has attention to detail. Every little detail in the work has a purpose and a reason. You might not pick it out, but it's there and can subconsciously elicit enjoyable responses from you, or if there is a lack of attention to detail a piece of work can elicit a negative response from you.
What I'm getting at is presentation, and more specifically presentation within the infosec community. The infosec community has a tough job, not only technically but also in getting people and organization to buy into information security ideas and solutions. Presentation is very important, not only within the community but also outside the community. I don't think the community's presentation is bad, in fact I've seen a lot of good presentations, but I do think it can be improved and I'm hoping that's something I might be able to contribute to.
For example (and the reason for this post):
I came across this website from CarolinaCon, a security conference in North Carolina.
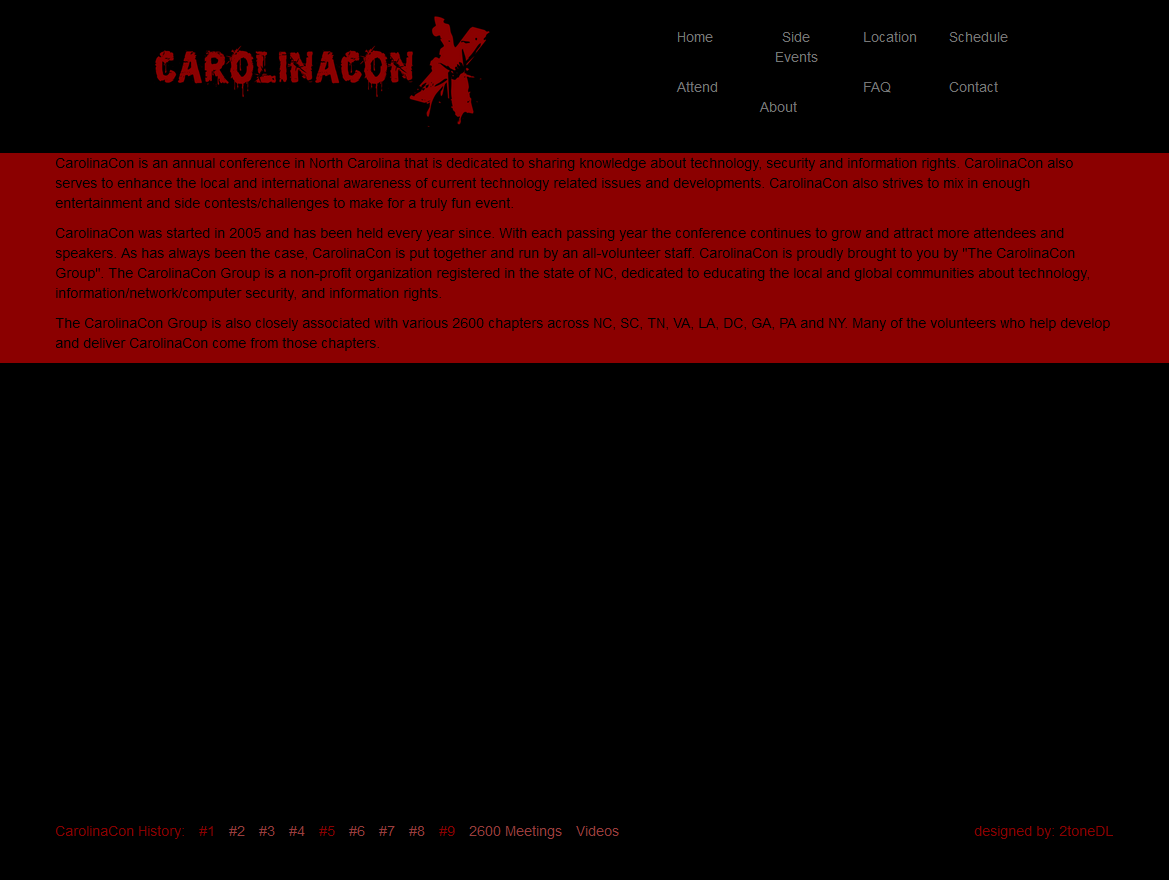
Now, before I critique this site I want to make note that I am trying to provide constructive feedback here. I am not calling the creator a dunderhead or the event stupid. I simply think the site can be improved. I absolutely love the logo. I think it's creative and unique to other security conference logos. I even like the colors, but what I don't like is using the colors for the rest of the website. Black on red or red on black or any other dark on dark colors is never a good combination for a website. Same goes for bright on bright colors. Gray on black is also not the best idea, but it's workable. The color scheme is a real eye sore and makes the whole website hard to read.
If we look at DefCon's, another security conference, website that uses black for it's background we see that they're using a lot of light blues and light purples. Which is much more pleasing to the eye.
They are using grey, but it's a much lighter grey in most places and the other light colors help balance it out.
Not to totally rag on CarolinaCon, it has built some pretty good websites in the past. At the bottom of their main page are links to some of the previous iterations of the site. Last years site was pretty good.
The light blue and orange on black is a good combination and the site is much more pleasing to navigate. The 2012 site is also much more pleasing to the eyes.
Like with anything we do in life, how much thought and effort you put into something is what you're going to get out of it. In regards to content you are presenting to others, it's also what other people are going to get out of it. If you want to get your message across, content needs to be created with the viewer in mind. They will essentially get out of it what you put into it. If content is just slapped on then it's going to feel like a slap to the face of the viewer and that can have a negative impact on your message.
Getting a media arts degree probably wasn't the smartest decision I made for my career, but I think I can make some use of it. I hope to do more posts like this that highlight and discuss some of the good and bad things done in presenting the information security message. If you have comments or questions please leave them in the comment section below or contact me directly. I would love to hear your thoughts.
This post first appeared on Exploring Information Security.
Nude photos of several female celebrities has apparently been leaked on 4chan, a message board that allows users to post content anonymously
Jennifer Lawrence's Nude Photos Leak Online, Other Celebs Targeted - Stephanie Marcus - Huffington Post.
A screenshot taken by New York Daily News of the forums post shows a list that includes:
Jennifer Lawrence - Hunger Games
Kate Upton - Model
Lea Michele - Glee
Lady Sybil [potentially Jessica Findlay] - Downton Abbey
Ariana Grande - actress/singer
Victoria Justice - actress/singer
Brie Larson - Don Jon
Kristen Dunst - Spiderman
Becca Tobin - Glee
Jessica Brown Findlay
Hope Solo - Soccer player
Teresa Palmer - Warm Bodies
Kristen [Krysten] Ritter - actress/model
Mary Elizabeth Winstead - actress/recording artist
McKayla Maroney - gymnast and internet meme
Yvonne Strahovksi - Chuck
Celebrity responses have ranged from acceptance, prosecution threats and outrage to straight up denials.

From what I've gathered so far, it appears as if the photos may have been uploaded to iCloud via Photo Stream and then compromised by someone. As we wait for more details, there are some warnings and lessons to be learned here.
Searching for nude photos on the celebrities above will increase your chances of getting some sort of malware on your computer. This is exactly the kind of big news that nefarious people will take advantage of to get something installed on your computer that could compromise it. Which could lead to several awful scenarios including your own nude photos being made publicly available.
Turn it off.
Unless you don't mind your photos being backed up on a server you have no control over, turn the automatic upload feature off. Googling 'disable Photo Stream automatic upload' should get you to some resources that will tell you how to do this.
Taking nude photos with a device that can potentially upload it to the internet is bad enough; having it upload automatically is simply not a very good idea.
Turn it on.
While we don't have all the details yet on how the pictures got stolen, it's possible that the theft could have been avoided if two-factor authentication was enabled. In cases like these, most of the time it's found that had two-factor authentication been enabled the compromise would not have happened. Two-factor authentication isn't perfect nor the ultimate solution, but it does increase difficulty of a compromise significantly.
Most applications and services you use have two-factor authentication available, use it. Apple and it's iCloud server has it available and it's fairly easy to setup.
Hash tags are the best thing since sliced bread and for events like these make the world a little brighter.
Get on Twitter and join in the fun.
This post first appeared on Exploring Information Security.
Major security skills shortages - Help Net Security
This post first appeared on Exploring Information Security.
Aaron's Law Is Doomed Leaving US Hacking Law 'Broken' - Thomas Brewster - Forbes
There is a general agreement, however, that the CFAA needs an urgent update. That’s largely because CFAA is being used against those trying to fix vulnerabilities on the internet. Various members of the security community, which is descending on Las Vegas for 2014’s BlackHat conference this week, have told me they have been threatened with law enforcement action over research efforts that were supposed to shore up the web and the machines connected to it. They include Zach Lanier of Duo Security and HD Moore of Rapid7, both highly-respected security pros. Given simply scanning systems for the infamous Heartbleed bug could have been deemed a felony, it’s become apparent that even those trying to do good are considered criminals.
Police are operating with total impunity in Ferguson - Matthew Yglesias - Vox
Olson was released shortly after his arrest, as were Reilly and Lowery before him. Ryan Devereaux from The Intercept and Lukas Hermsmeier from the German tabloid Bild were likewise arrested last night and released without charges after an overnight stay in jail. In other words, they never should have been arrested in the first place. But nothing's being done to punish the mystery officers who did the arresting.
Researchers Easily Slipped Weapons Past TSA's X-Ray Body Scanners - Andy Greenberg - Wired
More importantly, the glaring vulnerabilities the researchers found in the security system demonstrate how poorly the machines were tested before they were deployed at a cost of more than $1 billion to more than 160 American airports, argues J. Alex Halderman, a University of Michigan computer science professor and one of the study’s authors. The findings should raise questions regarding the TSA’s claims about its current security measures, too.
This post first appeared on Exploring Information Security.
In the sixth edition of the Exploring Information Security (EIS) podcast, I talk with PowerShell guru Matt Johnson a founder of PoshSec.
Matt Johnson has spoken at conference's like GrrCon and DerbyCon on using PowerShell for security. He also has his own podcast titled, Leveled up Infosec Podcast and he's the founder of PoshSec. You can catch Matt tweeting about security on Twitter @mwjcomputing.
In this interview we cover:
What is PowerShell
How to get started using PowerShell
How to best utilize PowerShell for security
Available resource
What mistakes can be made using PowerShell for security
Music by Alan Read
Leave feedback and topic suggestions in the comment section below.
This post first appeared on Exploring Information Security.
Father of PGP encryption: Telcos need to get out of bed with governments - Sean Gallagher - Ars Technica
Doing business with US government customers generally requires the use of National Institute of Standards and Technology (NIST) standards for encryption. But by default, Zimmermann said, Silent Circle uses an alternative set of encryption tools.
“It wasn’t because there was anything actually wrong with the NIST algorithms,” Zimmermann explained. “After the Snowden revelations, we felt a bit resentful that NIST had cooperated with the NSA."
Edward Snowden: The most wanted man in the world - James Bamford - Wired
Despite being the subject of a worldwide manhunt, Snowden seems relaxed and upbeat as we drink Cokes and tear away at a giant room-service pepperoni pizza. His 31st birthday is a few days away. Snowden still holds out hope that he will someday be allowed to return to the US. “I told the government I’d volunteer for prison, as long as it served the right purpose,” he says. “I care more about the country than what happens to me. But we can’t allow the law to become a political weapon or agree to scare people away from standing up for their rights, no matter how good the deal. I’m not going to be part of that.”
Why So Many Card Breaches? A Q&A - Brian Krebs - Krebs on Security
Today’s post includes no special insight into this particular retail breach, but rather seeks to offer answers to some common questions regarding why we keep hearing about them.
This post first appeared on Exploring Information Security.
70 Percent of World's Critical Utilities Breached - Help Net Security
This post first appeared on Exploring Information Security.
How To Protect Your Personal Information Online - The Onion
A fun list of ways to keep your personal information safe online.
Special Note: for those unfamiliar with The Onion, it is a satirical site and not meant to be taken seriously.
Social Engineering a Telemarketer - Bruce Schneier - Schneier on Security
Telemarketer gets owned and it's wonderful.
How to Use Your Cat to Hack Your Neighbor's WiFi - Andy Greenberg - Wired
Welcome to the infosec community my feline friend.
This post first appeared on Exploring Information Security.
Visit the Wrong Website, and the FBI Could End Up in Your Computer - Kevin Poulsen - Wired
The FBI’s use of malware is not new. The bureau calls the method an NIT, for “network investigative technique,” and the FBI has been using it since at least 2002 in cases ranging from computer hacking to bomb threats, child porn to extortion. Depending on the deployment, an NIT can be a bulky full-featured backdoor program that gives the government access to your files, location, web history and webcam for a month at a time, or a slim, fleeting wisp of code that sends the FBI your computer’s name and address, and then evaporates.
Scientists reconstruct speech through soundproof glass by watching a bag of potato chips - Jacob Kastrenakes - The Verge
While a bag of chips is one example of where this method can be put to work, MIT has found success with it elsewhere, including when watching plant leaves and the surface of a glass of water. While the vibrations that the camera is picking up aren't observable to the human eye, seemingly anything observable to a camera can work here. For the most part the researchers used a high-speed camera to pick up the vibrations, even using it to detect them on a potato chip bag filmed 15-feet away and through a pane of soundproof glass. Even without a high-speed camera though, researchers were able to use a common digital camera to pick up basic audio information.
Android Backdoor disguised as a Kaspersky mobile security app - Vigi Zhang - SecureList
Most email phishing attacks tend to target PC users, but this time the attackers have turned their attention to mobile platforms. We think it's a new trend in spreading virus. Mobile security is related to user privacy. In most cases, a mobile device is more important than PC for users. It contains user contacts, text messages, photos and call logs. And mobile security is generally considered to be a weak point. So, most people will believe these phishing emails and are likely to install the fake mobile security app.
This post first appeared on Exploring Information Security.
Hackers Unveil Their Plan to Change Email Forever - Denver Nicks - Time
Jon Callas, chief technology officer of Silent Circle and a co-founder of the Dark Mail project, told TIME that “the biggest problem we have today with email is that it was designed in the early 1970s and it was not designed for the problems we have today. Even the standard email encryption that we have today protects the content but not the metadata.”
You cannot 'cyberhijack' an airplane, but you can create mischief - Adam Greenberg - SC Magazine
Ultimately, airlines are very safe, Polstra said, but he added that nearly every protocol used in aviation is unsecured – meaning no encryption – and that there is potential to annoy air traffic control and small aircraft.
Founder of America's Biggest Hacker Conference: 'We Understand the Threat Now' - Denver Nicks - Time
Nothing changed before or after Snowden’s revelations. The security researchers knew that of course that’s what the NSA or any government can do. If you talked to the hackers last year it was like, “Of course you can do that. I’ve been doing that for 10 years.” But now that it’s sunken in at a more policy level you can have the conversation. Before you would say something to your parents and they’d be like, “Oh hahaha. You’re paranoid.” Next thing you know your parents are like, “Oh my God. You were not crazy. You’re not my paranoid son.” Now we’re at a place where people can relate and that’s a much more healthy place for us to be.
This post first appeared on Exploring Information Security.
In the fifth edition of the Exploring Information Security (EIS) podcast, I talk with J Wolfgang Goerlich, Vice President of Vio Point, about threat modeling.
Wolfgang has presented at many conference on the topic of threat modeling. He suggests using a much similar method of threat modeling that involves threat paths, instead of other methods such as a threat tree or kill chain. You can find him taking long walks and naps on Twitter (@jwgoerlich) and participating in several MiSec (@MiSec) projects and events.
In this interview Wolfgang covers:
What is threat modeling?
What needs to be done to threat model
Who should perform the threat modeling
Resources that can be used to build an effective threat model
The life cycle of a threat model
Leave feedback and topic suggestions in the comment section below.
This post first appeared on Exploring Information Security.