Emotet
Emotet was a highly sophisticated and notorious malware strain that was first identified around 2014 as a banking Trojan. However, over time, it evolved into a versatile and multifunctional malware platform that could be used for various malicious purposes beyond banking fraud. Emotet was primarily designed to steal sensitive information, such as financial credentials and personal data, from infected computers. It was known for its ability to spread rapidly and evade detection, making it a significant threat to individuals, businesses, and organizations.
Emotet primarily spread through malicious email attachments and links. Once a user interacted with a malicious attachment or clicked on a malicious link in an email, the malware would be downloaded and installed on the victim's system. Emotet's modular architecture allowed it to download and execute additional malicious payloads, such as ransomware or other types of malware, depending on the attacker's objectives.
One of Emotet's notable features was its ability to create a botnet—a network of compromised computers under the control of a central entity. This botnet could be used for various purposes, including sending out massive volumes of spam emails, distributing other malware, and carrying out distributed denial-of-service (DDoS) attacks.
In January 2021, a coordinated international law enforcement operation successfully took down the infrastructure behind Emotet. This takedown significantly disrupted the malware's operations and marked a major victory in the fight against cybercrime.
Podcasts
Created with help from ChatGPT
Stuxnet
Discovered in 2010, Stuxnet was a highly sophisticated piece of malware that targeted supervisory control and data acquisition (SCADA) systems used to control and monitor industrial processes. It is famously known for reportedly damaging Iran's nuclear program. Unlike typical malware, Stuxnet was designed to cause real-world physical effects by reprogramming industrial control hardware. It marked a significant moment in cybersecurity history as one of the first instances of cyber warfare where a digital attack had direct physical consequences.
Created with help from ChatGPT
Mirai
First emerging in 2016, Mirai is a botnet that targets Internet of Things (IoT) devices like digital cameras and DVR players, turning them into remotely controlled bots or 'zombies' that can be used as part of a botnet in large-scale network attacks. It was primarily used for conducting massive distributed denial of service (DDoS) attacks, including the infamous attack on the DNS provider Dyn, which resulted in widespread internet outages. Mirai highlighted the security vulnerabilities of IoT devices and the potential for new types of cyber threats exploiting these devices.
Created with help from ChatGPT
Pegasus is a highly sophisticated spyware developed by the Israeli firm NSO Group. It is designed to remotely infect smartphones, primarily running iOS and Android, and enable surveillance without the user's knowledge. Once installed, Pegasus can access calls, texts, emails, camera, microphone, and track the device’s location. It often exploits "zero-click" vulnerabilities, meaning the victim doesn’t need to interact with a malicious link or file for the malware to install. Pegasus has been used to target high-profile individuals, including journalists, activists, and political figures, raising serious concerns about privacy and human rights.
Created with help from ChatGPT
Pegasus
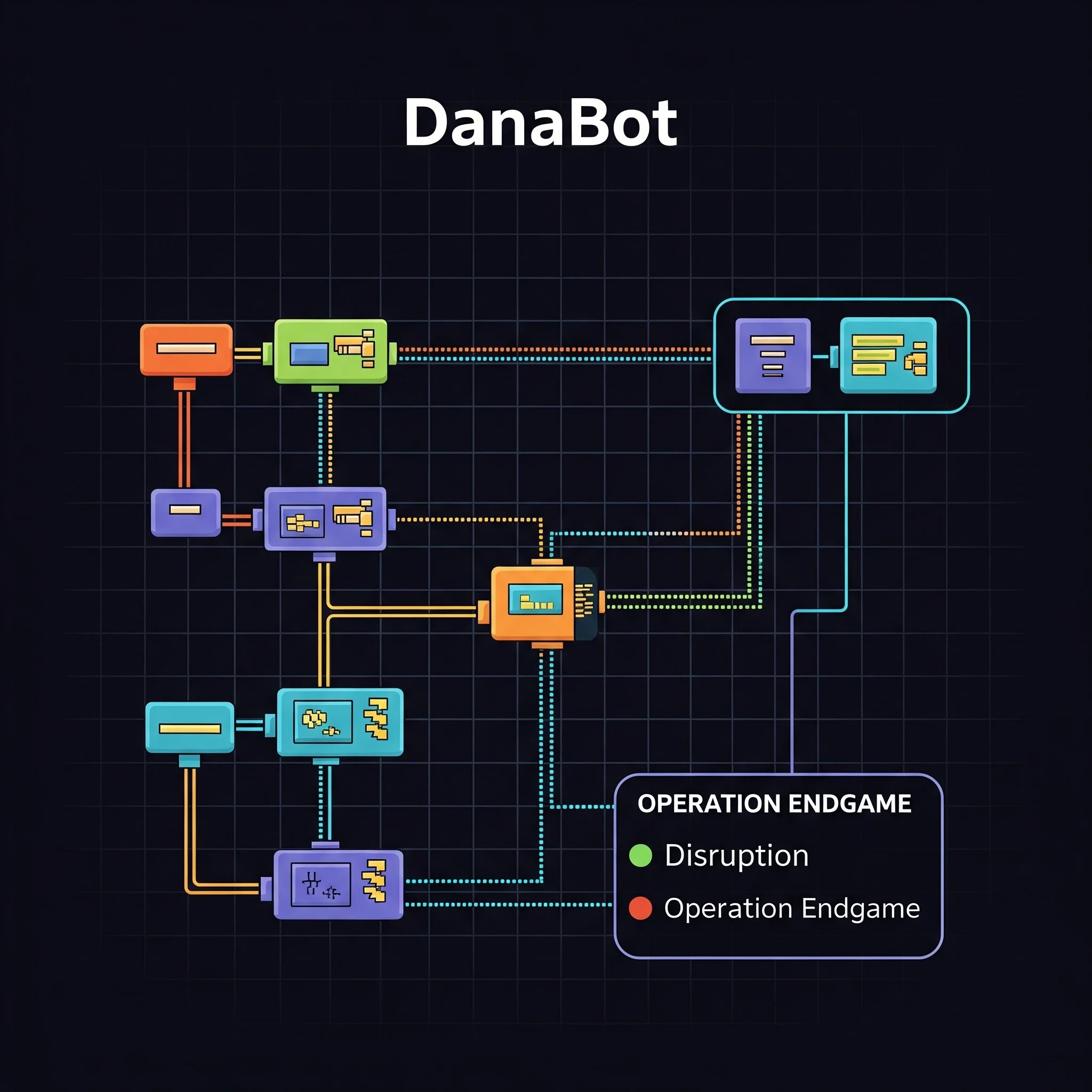
DANABOT
DanaBot is a sophisticated banking Trojan and infostealer that emerged in 2018, primarily designed to steal financial credentials and sensitive data. Known for its highly modular, Delphi-based architecture, it evolved into a versatile initial access broker, often used to deliver ransomware and other malware. Recently, in May 2025, its operations were significantly disrupted by "Operation Endgame 2.0," a major international law enforcement effort that took down its infrastructure and indicted key developers.
Created with help from Gemini